
Almost a third or 28% of data breaches in 2020 involved small businesses. The data comes from one of the most acclaimed cybersecurity reports in the industry, the Verizon Business 2020 Data Breach Investigations Report (2020 DBIR).
Currently, in its 13th year, the DBIR is an industry-standard when it comes to gauging the state of cybersecurity around the world. For this year’s report Verizon analyzed a record total of 157,525 incidents. Of those, 32,002 met the report’s quality standards and 3,950 were confirmed data breaches.
Small Business Data Breaches in 2020
With small businesses making up 28% of the breaches, owners have to be more proactive in protecting their digital presence. Whether it is an eCommerce site, blog, V-log, podcast, or other digital assets, you have to protect your domain. This not only ensures your data is safe, but it is one more tool you can use to attract new customers; robust security.
The Danger to Small Business
With that in mind, how are small businesses attacked in 2020? According to DBIR, the dividing line between small and large businesses is smaller today. The report attributes this to the movement toward the cloud and its numerous web-based tools, as well as the continued rise of social attacks. This has led the criminals to alter their forms of attack to get the information they need in the quickest and easiest way.
The COVID-19 pandemic is also responsible for the way businesses are operating. The surge of remote work is putting more companies at risk. This is what Tami Erwin, CEO, Verizon Business, expressed in the press release for the report.
Erwin says, “As remote working surges in the face of the global pandemic, end-to-end security from the cloud to employee laptop becomes paramount. In addition to protecting their systems from attack, we urge all businesses to continue employee education as phishing schemes become increasingly sophisticated and malicious.”
Small Business Attacks
The top patterns criminals are using to attack small businesses are web applications and miscellaneous errors. These represent 70% of the breaches. The threat actors who are perpetrating these crimes come mostly from external sources at 74%. Internal sources make up 26%, with partners at 1% and other multiple sources at another 1%.
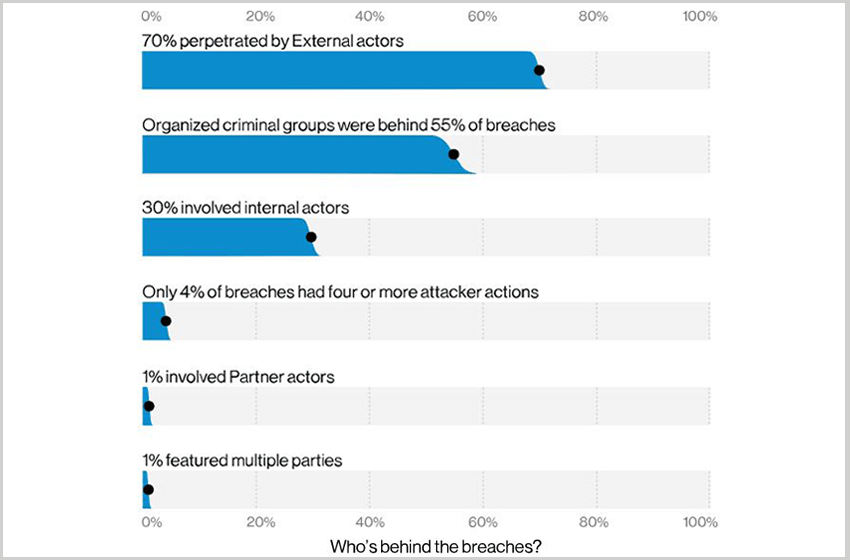
The data that is compromised is mostly made up of credentials at 52%. It is important to note these credentials later become part of other crimes. So, whether they are your credentials or that of your customers, you have to protect them. The other data are personal at 30%, other 20%, internal 14% and medical 14%.
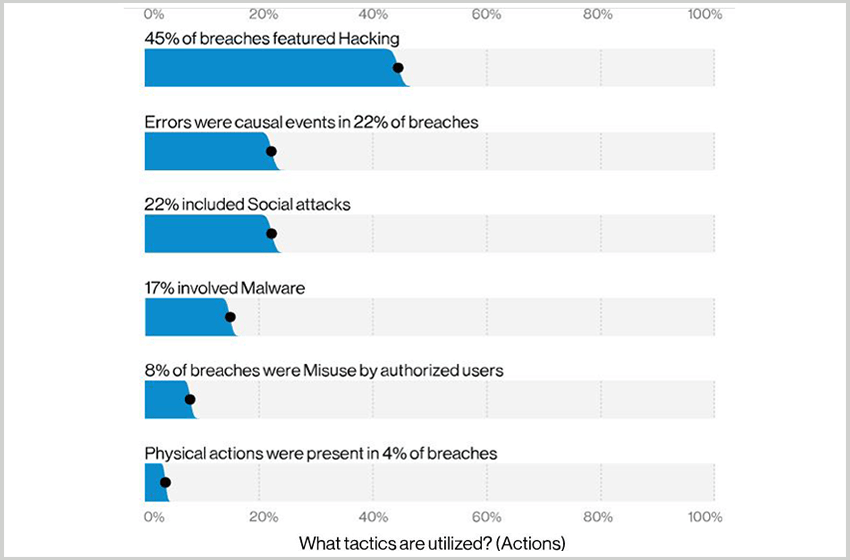
The threat actions are:
- Tampering (Physical) 7%
- Spyware (Malware) 46%
- Backdoor (Malware) 28%
- Export data (Malware) 29%
- Use of stolen creds (Hacking) 30%
- Use of backdoor or C2 (Hacking) 26%
- Capture stored data (Malware) 34%
- Phishing (Social) 22%
- C2 (Malware) 19%
- Downloader (Malware) 20%
- Password dumper (Malware) 17%
- Brute force (Hacking) 34%
- Rootkit (Malware) 18%
- Privilege abuse (Misuse) 8%
- Adminware (Malware) 15%
- RAM scraper (Malware) 15%
- Unapproved hardware (Misuse) 10%
- Embezzlement (Misuse) 10%
- Unknown (Hacking) 6%
- SQLi (Hacking) 4%
Recommendations
The report has some recommendations to keep your digital assets secure. And they are based on the findings with the Center for Internet Security (CIS) Critical Security Controls. The CIS CSCs is a community-built, attacker-informed prioritized set of cybersecurity guidelines that consist of 171 safeguards organized into 20 higher-level controls.
These are the following recommendations:
- Continuous Vulnerability Management—A great way of finding and remediating things like code-based vulnerabilities, such as the ones found in web applications that are being exploited and also handy for finding misconfigurations.
- Secure Configuration —Ensure and verify that systems are configured with only the services and access needed to achieve their function. That open, world-readable database facing the internet is probably not following these controls.
- Email and Web Browser Protection —Since browsers and email clients are the main way that users interact with the Wild West that we call the internet, it is critical that you lock these down to give your users a fighting chance.
- Limitation and Control of Network Ports, Protocols and Services —Much like how Control 12 is about knowing your exposures between trust zones, this control is about understanding what services and ports should be exposed on a system, and limiting access to them.
- Boundary Protection —Not just firewalls, this Control includes things like network monitoring, proxies and multifactor authentication, which is why it creeps up into a lot of different actions.
- Data Protection —One of the best ways of limiting the leakage of information is to control access to that sensitive information. Controls in this list include maintaining an inventory of sensitive information, encrypting sensitive data and limiting access to authorized cloud and email providers to authorized cloud and email providers
- Account Monitoring —Locking down user accounts across the organization is key to keeping bad guys from using stolen credentials, especially by the use of practices like multifactor authentication, which also shows up here.
- Implement a Security Awareness and Training Program —Educate your users, both on malicious attacks and the accidental breaches.
Key Findings in the Report
The overall findings in the report reveals 86% of data breaches are for financial gain, which is up from 71% in 2019. And most of these breaches (67%) are the result of credential theft, errors and social attacks.
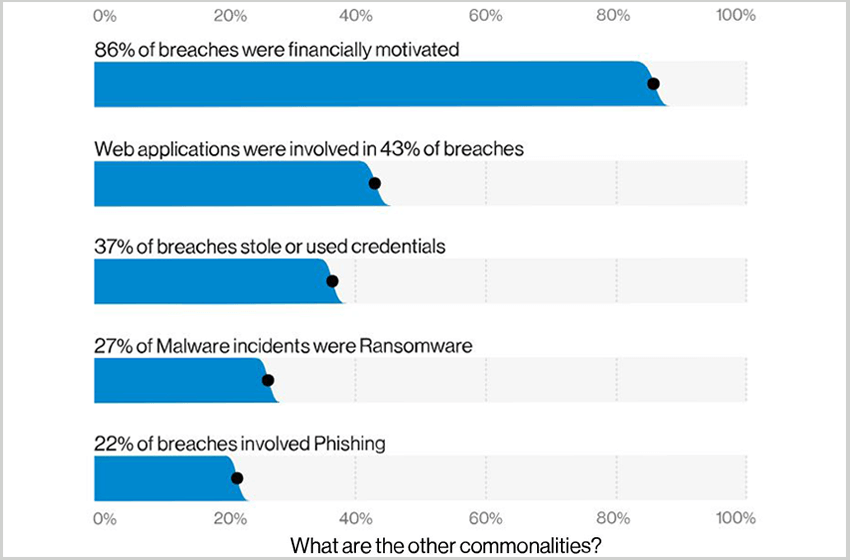
In retail, 99% of the incidents to gain financially from their attempts. Payment data and personal credentials are the end goal for the criminals. And to obtain this data they are targeting web applications instead of POS devices.
READ MORE:
Image: Depositphotos
This article, “28% of Data Breaches in 2020 Involved Small Businesses” was first published on Small Business Trends