Have you ever wondered about the future of passwords?
Around the world, hackers are jumping on the COVID-19 pandemic to spread malware and steal vital information. With an uptick in cyberattacks during lockdown, businesses are being warned to crack down on lax remote working practices. Failing to tighten up on security practices, especially as teams work remotely, can run the risk of catastrophic exposure to the hands of hackers.
The Future of Passwords
In 2019, 43% of cyberattacks were made to small businesses. With data hacking on the rise and small businesses being especially vulnerable to cybercrime, SMBs need to be vigilant in online security. One of the most effective ways to keep data safe is through effective password management.
With the growing emphasis on the importance of creating strong, unique passwords, now is a good time to look at the history and future of passwords. To shed light on the evolving world of digital passwords, online security innovators Beyond Identity composed an infographic.
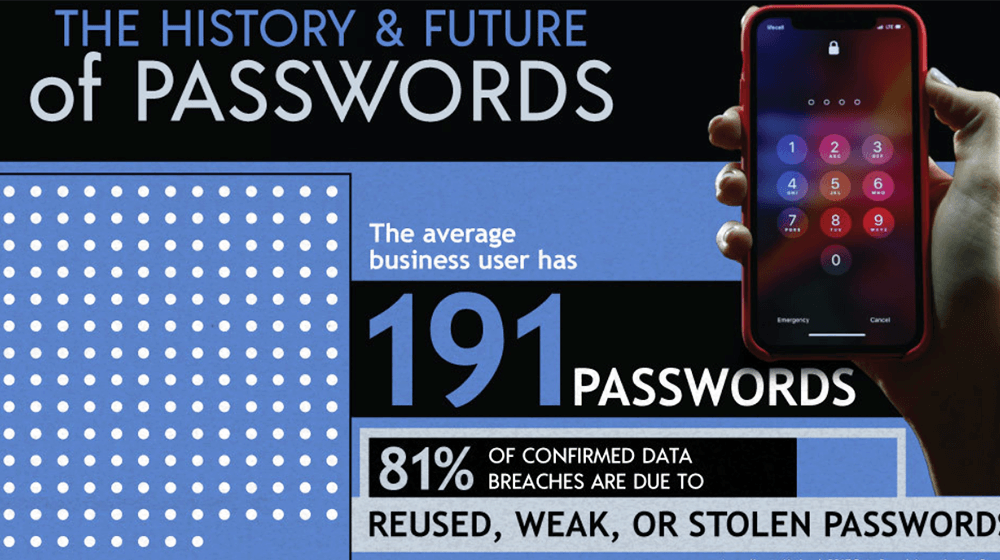
The ‘History and Future of Passwords’ infographic explores the history of passwords, as well as what might come after passwords. The research also highlights some startling facts surrounding the current usage of passwords.
66% of People Reuse Passwords
One such stat is that 91% of people know they shouldn’t reuse passwords but 66% do so anyway.
With cybercrime on the rise, reusing passwords in the current climate could be potentially devastating to small businesses. As Netscape co-founder and Beyond Identity founder Jim Clark says:
“All it takes is the breach of a site [to be compromised].”
1960: The First Password
The first password dates to 1960 with MIT’s Compatible Time-Sharing System (CTSS). The system relied on separate consoles to access a shared mainframe. Multiple users shared each console, each with their own set of files. A personal point of entry for each user necessitated the use of passwords.
1962: The First Password Theft
Just two years later was the first password ‘theft.’ PhD candidate Alan Scheer was given just four hours a week to work on the CTSS. Running the simulations he had designed required more time. To overcome the obstacle, Scheer printed the system’s password file so he could log on as other users.
One-Way Encryption
In 1974, we learned about one-way encryption. By translating passwords into numbers though one-way encryption, actual passwords were never stored on a device. This system is still in use today by the likes of PlayStation 4 ad macOS.
1980s: The Rise of Password Hacking
The infographic points to the 1980s as the decade when hacking started to spread its destruction. In 1988, the term the ‘Morris Worm’ was coined, which was the first computer worm on the internet. What was intended as a harmless experiment, the Morris Worm infected 1 in ten networked computers within 24 hours. As the infographic writes:
“The incident sparked a new era of cybersecurity and inspired a new generation of hackers.”
2011: Military Meltdown Monday
Fast forward to 2011 and the impact ‘Military Meltdown Monday’ had on digital passwords. On this dark day for online security, Anonymous hacked a contractor for the Department of Defense. The login credentials of 90,000 personnel were leaked, including military, State Department, Homeland Security, and private contractors.
Hacking the Tech
The infographic examines passwords getting hacked. It explains how hackers use tech to run through millions of passwords extremely quickly until one password works.
Hacking the Human
Another method hackers use is to hack the human. Rather than using tech, cybercriminals attempt to manipulate users into giving away their login details themselves. Such attempts include tricking users by posing as the likes of tech support. They also include phishing, whereby users download malware, click on suspicious links, or login through a compromised system.
Moving Beyond Passwords
With 66% of people admitting to reusing passwords despite knowing the risks, moving ‘beyond passwords’ could be the most effective way to stamp out cybercrime. Could certificate-based authentication eliminate the need for passwords in the future? This approach would put an end to guessable passwords. It also provides the same high-level security as TLS.
Risk-Based Authentication
Risk-Based Authentication determines if an access attempt is valid based on user identity, IP address, device security posture and geolocation.
Both of these methods significantly reduce the risk of hacking as they are void of any login credentials. Without any login details required, hackers cannot guess passwords and users cannot become targets of phishing attacks.
The History & Future of Passwords Infographic
READ MORE:
Image: beyondidentity.com
This article, “What is the Future of Passwords? (INFOGRAPHIC)” was first published on Small Business Trends